The storage system inside a PC, be it a diskette, a tape storage or a hard disk, consists of three logical parts. First part is the medium itself, that is the diskette, the cartridge tape or the hard disk. The second part is the mechanism that operates this medium—spins the disk or spools the tape. This is called the drive. The various kinds of drive are the floppy disk drive, the tape drive and the hard disk drive. The third part is the electronics, that controls the drive through commands given by the computer system. This is called the controller. In this section, you will learn about the floppy disk and hard disk systems.
Floppy Disk System
Floppy disks come in two sizes: 5¼ inch and 3½ inch. The 5¼ inch diskette is circular in shape with a hole in the center, called the clamping hole. It is covered with a square protective jacket. The jacket has an oval slot, called the head slot, which exposes a portion of the diskette surface. There is also a small hole near the center, called the index hole, which is the starting point of the diskette.
5¼ inch Floppy Disk
The diskette is inserted into the floppy disk drive, which is a sealed enclosure. It is clamped to the drive through the hub. The drive contains a spindle mechanism for rotating the diskette. It also contains another delicate piece of hardware called the read-write head that accesses the disk surface through the head slot and retrieves or stores data. The drive uses the index hole to sense the beginning of a track. The drive controller card supplies the drive with the necessary signals for its operations. For example, the controller tells the drive when to move the read-write head, when to start rotating the disk, and so on.
A 3½ inch diskette, also called as the microdisk, is also circular in shape and is covered with a square protective jacket. The media cover is pushed to expose the diskette surface. The operations are similar to those of 5¼ inch diskettes. A 3½ inch diskette is shown in Figure.
A 3½ Inch Diskette
A diskette is divided into a series of concentric circles called tracks. The tracks are identified by numbers, with the outermost track as track zero. The tracks do not spread across the whole width of the recording surface, but take up a small area. The track is divided into sectors. Each sector is identified by a number that is assigned to it, starting with zero. Each type of floppy has a sector of a fixed size. A disk has two sides. Data can be recorded on either one or both sides of the disk.
The storage capacity of a disk is determined by factors like the number of tracks, sectors and the number of sides on which data is recorded. Depending upon the capacity of storage, the 5¼ inch diskettes are divided into double-density (360 KB) and high-density (1.2 MB).
The microdisk may be double-density (720 KB) or high-density (1.44 MB). Accordingly, disk drives can be double-density or high-density drives. A high-density drive can read and write on to a double-density diskette but the reverse is not possible.
Hard Disk System
The hard disk is made up of a collection of disks known as platters. It is sealed in a vacuum container, and is located inside the system unit. When the tracks having the same track number on the different platters of a hard disk are joined together, they form a cylinder.
The read-write mechanism in a hard disk is slightly different from that of a floppy disk. Here, the read-write arm (containing twice as many read-write heads as there are platters, since each platter has two recording surfaces) is positioned over the recording surface and the disk is rotated. The read-write head then picks up the necessary data, which is transported to the RAM through the data bus. The hard disk controller performs functions similar to that of a floppy disk controller.
Display Adaptors
Various kinds of monitors are available—black and white or color—some displaying sharper images than others. Images are formed on the monitor's screen by a card called the display adapter card.
The key elements of a display adaptor are the video controller and the memory. As you know, the results of your interaction with the PC are displayed on the screen of the monitor. The information to be displayed on the monitor need to be stored somewhere so that it can be displayed. The memory on the adaptor card holds this data. The video controller is responsible for forming the image on the screen using this data. This memory is also accessible by the microprocessor so that changes can be made to the data when required. The time taken for reading the display memory and displaying a new picture on the screen is roughly one-fiftieth of a second. If a program wants new information to be displayed, it places the data in the display memory and it is reflected almost instantaneously on the screen.
Several kinds display adaptors exist in the market, each with its own special features. Some of the parameters that are used to distinguish between the various display adaptors are:
- Display in text mode
- Resolution in graphics mode
The PC can represent data on the screen in two modes. One is the text mode in which only text or individual characters can be displayed. The other is the graphics mode, where graphics (pictures) can be shown by constructing an image on the screen using dots.
In the text mode, the VDU screen is divided into specific character positions—usually 80 columns—of characters across the width of the screen and 25 lines of characters from top to bottom. Most, but not all, display adaptors support display of text on the screen.
In the graphics mode, the screen is treated as an array of tiny dots called pixels (short for picture elements), and anything that appears on the screen is shown using these dots. Each of these dots can be set on or off on the screen.
In the graphics mode, a parameter that can further differentiate between various display adaptors is resolution. Resolution of the screen indicates the number of dots or pixels on the screen. A typical high resolution display has 640 columns of dots across and 480 rows of dots down the screen. Besides, the display adaptors, that support graphics, have different resolutions. The higher the resolution (i.e. more the number of pixels), the better the quality of pictures displayed on the screen.
Yet another parameter used to differentiate between display adaptors is whether they support color or not. There are two types of monitors—monochrome (i.e. black and white) and color.
The monitor you have needs to be compatible with the adaptor card. It would be no use having a color monitor with a display adaptor that does not support color; or having an adaptor that supports high resolution with a low resolution monitor.
Since the resolution and the number of colors increase with increasing sophistication of display adaptors, the pixels require increasing amount of memory. Thus, the amount of memory on the display adaptor has to be increased.
Having considered the main parameters used to evaluate the display adaptors, you will now study some of the popular display adaptors supported by the PC.
=> Enhanced Graphics Adaptor adaptors (EGA)
Enhanced Graphics Adaptor (EGA)
EGA or Enhanced Graphics Adaptor is an effort to unify features of a variety of display adaptors. The EGA combines all the features of the above adaptors and provides higher resolutions. It supports upto 16 colors at a time. The EGA could have been a replacement for the other adaptors except for the fact that it is expensive and is not supported by specific software provided by some vendors. An EGA usually has a resolution of either 640 x 200 pixels or 640 x 350 pixels. In order to make the best use of an EGA, you need to use a high quality color monitor.
Enhanced Graphics Adaptor (EGA) Card
Video Graphics Array adaptors (VGA)
Video Graphics Array adaptors (VGA) are currently used because they produce high quality graphics. The VGA adaptor provides up to 256 colors and also a high resolution. There are two typical combinations of resolution and color that a VGA provides:
- 640 x 480 pixels with 16 colors
- 320 x 200 pixels with 256 colors
The resolution and colors of various display adaptors can be different from the values given above, depending on who manufactures them. The VGA, like the EGA, is quite expensive.
Video Graphics Array (VGA)
Super Video Graphics Array (SVGA)
The Super Video Graphics Array adaptor, as the name suggests, is an improvement on the VGA. There are many combinations of resolution and color that a SVGA provides:
- 640 x 480 pixels with 256 colors to 65536 colors
- 1024 x 768 pixels with 256 colors
- 800 x 600 pixels with 256 to 65536 colors
- 1280 x 1024 pixels with 16 colors
Super Video Graphics Array (SVGA)
Add-on Cards
Computers can also handle special functions like producing music, reproducing video clippings on the VDU, even though they are not normally programmed to do so. In such situations, you have to install a special piece of hardware on the motherboard, so that your PC is able to perform these functions. The special piece of hardware which is called an add-on card, is responsible for the communication between your PC and other electronic devices like TVs, VCRs, audio-systems, etc.

One such add-on card is the audio-card. This card allows audio speakers to reproduce sound/music based on instructions from the motherboard. It also allows you to control the volume and tone of the Sound/music, which is not possible using the in-built speaker. Popular brands of audio cards in the market include Sound Blaster .COVOX and Aztec.
Similar to the audio card is the video-card. It does a two-way transfer of images from the system unit to a TV/VCR for recording or playback. The text ( For example, title, cast names etc.) that appear in movies is made possible using this card. Computer Eyes and TARGA are the commonly-used video cards.
Multimedia relies on the ability of these cards to transfer sound and pictures to and from the PC and microphones, audio cassette players, speakers, VCRs and video cameras. Multimedia software lets you integrate voice and visuals into your programs. Such applications are used in training and in business presentations.
The PC Range
Computers falling under the class of PCs can be classified into two broad groups - the desktops and the portables. Desktops cannot be carried around and used while you are traveling. The portable is designed for this purpose. Examples of desktop PCs are IBM's PS/2 systems and Apples' Macintosh range of computers. Their application areas are the same as those listed for micros.
Characteristics of Portables
Portable computers are productivity-enhancement tools that allow busy executives to carry their office work with them. Thus, the time spent in waiting for planes, trains, etc. can be used productively as the office travels with the executive.
The critical criterion for a portable computer is size. The smaller the size, the easier it is to carry around. Several innovative techniques are being used to reduce size, some of which will be discussed here.
The VDU has to be compact, light, and use less power (these computers are meant to be used on the road and, hence, run on batteries). For this, LCDs (Liquid Crystal Displays—the kind you see in calculators and watches) that are light and consume very little power, are used.
The number of keys on the keyboard are reduced, and the keys are made to perform multiple functions. As the keyboard cannot be shrunk indefinitely, other devices like the mouse, light pens, etc. are used.
The size of hard disk is reduced. Hard disks as small as 2.5" in diameter but capable of storing large quantities of data and weighing only 300 gms are available.
The size of hard disk is reduced. Hard disks as small as 2.5" in diameter but capable of storing large quantities of data and weighing only 300 gms are available.
There are however, problems which have to be tackled. When using portables in office, the user would like to utilize resources of the desktop. The desktop can be used by swapping its hardware with that of the portable. One option is to have a desktop PC in the office and use the portable while travelling. But this involves swapping disks in and out to transfer data. Some portables overcome this problem by providing docking stations. All you have to do now is to plug the portable into the docking station, and you can use normal screens and keyboards. This has the added advantage of avoiding duplicate system units.
A Portable Computer
If carrying the office with you is to be made a reality, the portable should allow you to communicate with your base office (which is stationary) while you are on the move. Most portables allow modems to be fitted inside them or provide sockets for an external connection to a modem.
Note: A modem which stands for modulation-demodulation is a device that converts the digital pulses into analog pulses when telephone lines are used to transmit data.
Classes of Portables
There are essentially three classes of portables: laptops, notebooks and palmtops.
Laptops are of the size of a small, slim attache case and weigh around 7 to 12 kg. They offer the same power as a desktop machine. These are essentially scaled down desktops, and use a reduced keyboard and mouse as input devices. The disadvantage of a laptop is that it is bulky. It is also very difficult to operate a mouse without a desk. Examples of laptops are Toshiba 5200C from Toshiba and SLT/286 from Compaq Computer Corporation.
Laptop
Notebooks have been designed to overcome the disadvantages of a laptop. Notebook computers are about the size of a notebook (approximately 21 x 29.7 cm.) and weigh about 3 to 4 kg. Notebooks also offer the same power as a desktop PC. Examples of notebooks are Contura 3/20 from Compaq, and AcerAnyWare from Zenith Computers Ltd.
Notebook
Palmtops are the smallest of portables and are normally the size of a pocket calculator. These, however, do not offer the same power as that of a PC. The applications are limited and built-in, for example, Hewlett Packard's HP95LX comes configured with LOTUS 1-2-3, a spreadsheet. They are useful for data entry operations in the field.
Palmtop
Ambiguity in Classification
Although this classification of computers was fairly rigorous till about 10 years ago, the rapid advance in technology has blurred the distinctions between these categories. For example, the technical definition of a microcomputer is a computer that uses a microprocessor for its main processing activities. But now-a-days, even mainframes and supercomputers use a collection of standard microprocessors. A computer at the higher end of the microcomputer range may possess the power of a minicomputer, and support more than one user at a time, but cost less. Soon we may have microcomputers which may outperform the mainframe of today. A mainframe may have the same processing power of a lower end supercomputer.
Classification of Computers
Computers vary widely in performance, size and cost. Depending upon these parameters, the computer industry classifies them into the following categories:
- Microcomputers (also referred to as micros)
- Minicomputers (also referred to as minis)
- Mainframes
- Supercomputers
The performance of a computer is measured in terms of speed of processing instructions, data storage capacity, ability to handle a large number of input and output devices, and the nature of operations it can perform (simple word processing to complex scientific calculations). Generally, computers with better performance are larger in size and cost more than computers with less processing power.
Microcomputers
Microcomputers are at the lowest end of the computer range. The highly visible personal computers you see on desktops fall into this category.
Microcomputers are typically single-user systems, which means that only one user can use it at any time. Microcomputers have small to medium data storage capacities (500 MB-2 GB). Their processing power is also limited in terms of the number of instructions that they can process per second. Therefore, they are not suitable for applications that require large storage capacities and involve complex mathematical calculations, such as weather forecasting or aircraft design.
Apple Macintosh
The most common applications of the PC are word processing, spreadsheet calculation and database management. The other applications are desktop publishing (using computers for publishing), accounting, statistical analysis, graphics designing, investment analysis and project management. Microcomputers are also used in the field of teaching (the computer acts as a teacher) and entertainment (computer games).
Examples of desktop PCs are: IBM PC, PS/2 and Apple's Macintosh.
Minicomputers

Minicomputers perform better, are larger in size, and cost more than micros. Normally, they are designed to support more than one user at a time. They possess larger storage capacities and operate at higher speeds. They support faster peripheral devices like high-speed printers, which print hundreds of lines per minute. They can also communicate with mainframes.
These computers are used when the volume of processing is large; for example, data processing for a medium-sized organization. They are used to control and monitor production processes, to analyze results of experiments in laboratories, to meet instructional needs of colleges, etc. They are also used as servers in Local Area Networks (LANs).
Examples of minis are: Digital Equipment's PDP 11/45 and VAX 11.
Mainframes
Mainframes are more powerful than minis. They operate at very high speeds, have very large storage capacities and can support hundreds of users.
They are used for data processing in large organizations where the records of thousands of employees have to be processed. They are also used to manage large centralized databases. Such databases are normally queried by hundreds of users who need to access information from different locations. They are used as controlling nodes in Wide Area Networks (WANs).
Examples of mainframes are: IBM 3000 series, Burroughs B 7900 and Univac 1180.
IBM Mainframe
Supercomputers
Supercomputers axe at the apex of the computer range. They are the fastest and the most expensive machines, and are considered a national resource. Although initially used for weapons design, they are also used for commercial purposes, like designing automobiles that will offer better protection to passengers in case of accidents. They are required (and can be afforded) only by a few organizations. There are less than 500 conventional supercomputers in the world.
 One of the ways in which supercomputers are built is by interconnecting hundreds of microprocessors (the tiny chips which perform all the calculations in your PC), and making them function in parallel. These computers are capable of performing billions of calculations per second.
One of the ways in which supercomputers are built is by interconnecting hundreds of microprocessors (the tiny chips which perform all the calculations in your PC), and making them function in parallel. These computers are capable of performing billions of calculations per second.
Some of the areas in which supercomputers are being used are weather forecasting, biomedical research, and aircraft design.
Predicting the weather involves analyzing thousands of variables gathered by satellites, aircraft and other meteorological stations on the ground. This analysis has to be done in a very short time. There is no point in producing a cyclone warning after the cyclone has hit. A supercomputer is the answer to this problem.
In the medical field, supercomputers are used to study the structure of viruses, such as those causing AIDS.
Designing an aircraft involves simulating and analyzing the airflow around the aircraft. This again requires a supercomputer.
Examples of supercomputers are: Paragon from Intel Corp. USA, Supercomputers Systems Division from nCube USA, 2S from nCube, Cray models from Cray Research, and Param from C-DAC India.
Paragon from Intel Corp.
Storage Media
Data needs to be stored for later use on storage media. If the volume of data that needs to be stored is small, floppy disks are enough. However, when the amount of data to be stored is huge, storage media with larger storage capacities are required. In this section, you will learn about three such storage media - Cartridge Tape, CD-ROM and Magneto-optical disks.
Cartridge Tape
Assume that an organization has bought a powerful computer to meet its growing needs. The problem now is to shift the massive databases (e.g. a collection of related files, in which an employee database can contain employee code file, attendance file, loan file, leave file, etc.) from the old machines to the new ones. Using diskettes as the backup medium is cumbersome, as they cannot store large amounts of data. In such cases, a cartridge tape is a very convenient backup media as it can store many megabytes of data. Cartridge tapes are available in capacities of 60 MB, 150 MB and 500 MB.
Cartridge Tape
A cartridge tape is made of plastic, coated with a magnetic material, and is similar to a video cassette tape. The tape is divided into tracks, which run along the entire length of the tape. Data is recorded along these tracks. Just as you need a disk drive to read or write data onto a disk, you need a cartridge tape drive which is an input-output device for a cartridge tape.
Data on a cartridge tape is stored sequentially. Therefore, if you want to access data stored at the end of the tape, you will have to run through the entire tape till you come to the end. This is in direct contrast to accessing data on disks wherein data can be accessed randomly. A good analogy here is the audio tape or the gramophone record. If you want to listen to a song recorded in the middle of the tape, you have to forward the tape till you come to the point where the song starts whereas in the gramophone record you can directly place the gramophone head on the required sound track. Cartridge tapes are used wherever the volume of data or software to be backed up is very large, for example, backup copies of DBMS. Cartridge tape drives are present only in large machines.
CD-ROM
Imagine that you are viewing a video film about an Antarctic expedition on your computer. It would be ideal if you can see the recording of the expedition, hear a commentary on the expedition at the same time and listen to the conversation of members of the expedition on your computer. All this and more is possible using a CD-ROM (Compact Disk Read Only Memory) as a storage medium. The CDs used in a CD-ROM are similar to audio CDs and can store vast quantities of data—600 MB or more
To read a CD-ROM, you need an input device called the CD-ROM drive. A CD-ROM can not be erased or written onto without the help of a special device called the CD-Recorder.
CD-ROM and CD-ROM Drive
CD-ROMs are used whenever large volumes of data need to be stored and distributed. Databases on medicine, tourism, literature, etc. are available on CD-ROMs. Encyclopedia and dictionaries are also available on CD-ROMs.
Magneto-optical Disk
The data storage requirements of organizations have increased manifold. Software has also become powerful and, at the same time, voluminous. With usually more than several hundred megabytes or even gigabytes, the storage capacity of 1.44 MB diskette is insufficient.
Maxell Corporation, USA, has developed a 314 inch Magneto-optical (M-O) disk, having storage capacities in excess of 640 MB. M-0 disks with capacities of 2 GB are also available. Data can be read as well as written onto these disks. The new disks are compatible with all 3W inch magneto-optical drives, such as those manufactured by Fujitsu, Olympus, and others. Some of the significant improvements of the M-0 disk over the conventional 1.44-MB diskette are:
- Write speed that is more than 100% faster than the speed of conventional media. This is achieved by bypassing the erase data phase during a rewrite operation. Thus data can be directly overwritten on existing data during an overwrite operation.
- If the M-O disk is double-sided, it can store up to 4GB of data, which is more than what many hard disks can store.
- An archival life of more than 30 years, the disks are rewriteable over 1 million times.
- Protective layer of exceptionally durable hard coating to safeguard surface from heat or moisture.
Some applications of the new M-0 media include: mass archival storage, document/image storage, and multimedia storage using data compression technology.
Magneto-optical Disk
Now that you have become familiar with the PC environment, you will see where the PC fits in the computer spectrum. You will be given a bird's eye view of the computer range, from micro-computer (of which the PC is a well-known example) to supercomputers, the emphasis being on their capabilities and application areas. In this session, you will also take a closer look at the PC range itself.
Mouse
A mouse is an input device that is used to point and select an option on the VDU. A mouse can be classified on the basis of the number of buttons it has, the technology it uses and the kind oi interface it has with the computer.
A mouse may have one, two or three buttons. The function of each button is determined by the program that uses the mouse. A software package may use one, two or all three of them. In its simplest form, a mouse has one button. Moving the mouse on a flat surface produces a corresponding movement of a pointer on the screen. Placing the pointer on an option and clicking the button results in selecting that option.
Two-button Mechanical Mouse
A mouse may be classified as a mechanical mouse or an optical mouse, on the basis of the technology it uses. In a mechanical mouse, the ball that projects through the bottom surface rotates as the mouse is moved along a flat surface. The direction of rotation is detected and relayed to the computer by the switches inside the mouse. Microsoft, IBM and Logitech are some weil-known makers of the mechanical mouse.
An optical mouse uses a light beam instead of a rotating ball to detect movement across a specially patterned mouse pad. MSC Corporation makes the optical mouse that uses LEDs and photo-detectors to trap movement.
Scanners
Another input device that is being increasingly used is the scanner. Often, there are situations when some information (picture or text) is available on paper and is needed on the computer disk for further editing. The simplest way would be to take a photograph of the image directly from the source, and convert it into a form that can be saved on the disk and then printed.
Flat-bed Scanner
A scanner scans an image and transforms the image to ASCII codes that is the code used by a computer to represent the characters you find on your keyboard—letters of the alphabet, numbers, punctuation marks and graphics. These can be edited, manipulated and printed.
Scanners are of two types—the flat-bed type and the roller-feed type. While in a roller-feed scanner, the image is passed over a roller where it is captured, the flat-bed scanner works like a photo-copier. Flat-bed scanners can scan and store images from books without having to remove the page, which is difficult in the case of the roller-feed scanner.
Many of the scanners available now-a-days are capable of not only scanning text and graphics, but also integrating text and graphics files.
Scanners are used to reproduce photographs on the computer screen. They can be employed in training programs using the computer and in desktop publishing. Businesses use scanners for storing documents on the computer.
Touch Screens

Imagine a cardiac surgeon performing an intricate bypass surgery. In between, the surgeon needs to check on the laboratory test results of the patient. Assuming that the information is stored on a computer, the surgeon can access the information through a keyboard, or better still, through a mouse. But how much more convenient it would be if the surgeon could only touch the screen on the option that is required to display the information. A touch screen input interface does exactly this. Touch screens are normally used when information has to be accessed with minimum effort.
Two popular technologies exist for touch screens. In one, the screen is made sensitive to touch and the exact position is detected. In the other, the screen is lined with light emitting devices and photo-detectors. When the user's finger approaches the screen, the light beam is broken and is detected by the photo-detectors.
Touch screens are used in information-providing systems like the one explained above. It is also used in airline and railway reservation counters. The users indicate their current location and the destination by touching the screen (maybe on a map), and all the possible routes with timings and rates are displayed. These interfaces are also used in travel agencies to display the names and addresses of all hotels, restaurants, and other places of interest, at a desired destination. Touch screens are also used in stock exchanges.
Light Pens

A light pen is a pointing device that can be used to select an option by simply pointing at it, or drawing figures directly on the screen.
A light pen has a photo-detector at its tip. This detector can detect changes in brightness of the screen. When the pen is pointed at a particular spot on the screen, it records change in brightness instantly and informs the computer about this. The computer can find out the exact spot with this information. Thus, the computer can identify where you are pointing on the screen.
Light pens are useful for menu-based applications. Instead of moving the mouse around or using a keyboard, the user can select an option by pointing at it.
A light pen is also useful for drawing graphics in CAD. An engineer, architect or a fashion designer can draw directly on the screen with the pen. Using a keyboard and a light pen, the designer can select colors and line thickness, reduce or enlarge drawings, and edit drawings.
Printers
Printers are output devices that print the result of an operation on paper. A printer is capable of producing output that contains printed words. It is also capable of printing straight lines and simple figures like squares, rectangles and circles. Printers are classified based on a number of parameters, like the mechanism used for printing, the speed of printing, the quality of output, the direction of printing, and the kind of interface they have with the computer. The following sections will elaborate on these parameters.
Mechanism
Depending upon the technique used for printing, printers can be classified into two broad categories - impact and non-impact printers.
In impact printers, characters are printed by pressing a typeface against an inked ribbon, which makes a mark on the paper. The most commonly-used impact printer is the Dot Matrix Printer (DMP).
In a DMP, an arrangement of tiny hammers or pins strike the ribbon to produce the desired characters. These tiny pins typically print in a matrix of 7 dots across and 9 dots down. The impact of the appropriate pins on paper through the inked ribbon forms letters made up of dots. There are printers which use up to 24 vertical pins to print characters with a higher resolution.
Dot Matrix Printer
DMPs are inexpensive but noisy. They can print both text and graphics. They can print in any language without additional hardware. They can also be made to print in color by changing ribbons. These printers are used to produce internal reports and memos needed by organizations. The other types of impact printers are drum printers, daisy wheel printers and golf ball printers. However, these printers are not as popular as DMPs.
Examples of DMPs are: CENTRONICS-702, HP-2635A, OLIVETTI TC480 and Epson LX-80.
In non-impact printers, there is no contact between the typeface and the paper while printing. An example of a non-impact printer is the laser printer.
Laser printers use a light beam to form images on the paper using toner ink as the medium. The light beam strikes parts of a drum surface to form an image. Those parts of the drum surface, which are exposed to the light beam, become electrically charged. Only these electrically charged areas attract the toner ink particles. These toner particles are then deposited on, and permanently fixed to the paper using heat or pressure.
The other types of non-impact printers are thermal printers that use heat to print characters on paper and ink-jet printers that use jets of ink to print characters on paper.
Laser Printer
Laser printers generate a very high quality output, both text and graphics, and are typically used for publishing. Most organizations use them for business correspondence, newsletters, brochures and presentations. Laser printers are expensive.
Examples of laser printers are: Xerox 4010 from Rank Xerox UK, LASERJet IlISi from Hewlett Packard USA and Lexmark Optra from Lexmark USA.
Speed
The speed of a printer is measured in terms of characters per second (cps), lines per second (Ips) or pages per minute (ppm). The speed of a dot matrix printer is measured in cps. The speed can vary from 200 cps to 540 cps. A line printer prints a line at a time. Its speed can vary from 5 to 50 Ips. A laser printer prints within the range of 4 to 20 ppm.
Quality of Output
Printers can operate in three different modes—draft, Near Letter Quality (NLQ), letter quality.
In the draft-quality mode, a DMP forms a character by arranging dots to assemble it. Although the characters can be distinguished, the output is not as good as that of near letter quality printouts. A laser printer prints in the draft mode by using less toner ink to form the characters.
For printing in letter quality, the DMP prints a character twice, thereby making its appearance darker. A laser printer prints in the letter quality by using more toner ink than it uses while printing in the draft mode.
Direction
Dot matrix printers and ink-jet printers can be unidirectional, bidirectional, or reverse. In a unidirectional printer, printing takes place in one direction only. After printing a line from left to right, the printer head (the component that carries the pins or characters) returns to the left without printing.
A bidirectional printer prints both ways, with logic-seeking capability, i.e. it selects the characters in the reverse direction while printing in reverse. A reverse printer has no such capability, and expects the computer to supply the characters in reverse order.
Interface
Depending upon the number of characters received at a time, printers can be serial or parallel. Serial printers are slower than parallel printers. A serial printer receives one character at a time for printing. A parallel printer receives more number of characters and is faster.
Plotters
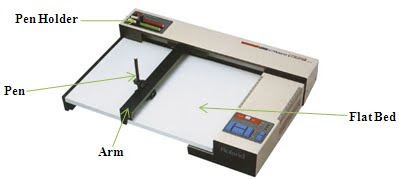
Very often it might be required to create high-quality visuals on paper, which cannot be obtained using a printer. For this purpose, a plotter is used. A plotter is an output device that is used to create presentation visuals, charts, graphs, tables and diagrams.
A plotter consists of an arm that moves across the paper on which the diagram or graph needs to be drawn (refer Figure). A pen moves along the arm, and the arm itself moves relative to the paper. A combination of the two thus provides movement along the horizontal and vertical axes.
Flat-bed Plotter
In some plotters, the paper is held stationary while the arm and the pens move over it. This is called a flat-bed plotter. In the other type of plotter, the paper is wrapped around a drum and anchored at both ends. The drum rotates while the pen moves laterally along a fixed rail. This is called a drum plotter.
To draw clear, high-quality diagrams, a plotter needs high-quality pens with special inks of different colors.
A plotter can be connected to a PC through the parallel port. A plotter is more software-dependent than any other peripheral, and needs much more instructions than the printer for producing output.
Plotters are used in applications like Computer Aided Design (CAD) which require high-quality graphics on paper. Many of the plotters now available in the market are desktop models that can be used with PCs. Businesses typically use plotters to present an analysis in visual terms (bar charts, graphs, diagrams, etc.) as well as for engineering drawings.
NetWare Commands
Some of the NetWare commands are:
| COMMAND | REMARKS |
| NDIR | To view contents of a directory |
| RENDIR | To rename a directory |
| NCOPY | To copy files |
| PURGE | To delete files permanently. PURGEd files cannot be Salvaged |
Other NetWare Utilities
SALVAGE is not the only menu-driven utility offered by NetWare. There are others, like FILER and SYSCON, which can be extremely useful to you. In this session, you will learn to use the FILER utility.
The FILER Utility
This utility is used to control Volume, Directory and File information, and to change File and Directory security. On invocation, a menu as shown in Figure is displayed.
FILER - Main Menu
A brief note on some of the options available with this utility are included.
| Follow Up Next |
Current Directory Information
As an ordinary user, this option enables you to get the currently active directory's details such as ownership, date and time of creation, attributes, rights—effective, inherited as well as trustee. If the directory in question belongs to you, you can alter inherited rights, attributes and grant trustee rights to other users. As the supervisor, you can alter any of the directory details. A sample screen is shown in Figure.
FILER - Directory Information
| Follow Up Next |
Directory Contents
This option allows you to do some of the tasks you are already familiar with, like deleting, copying, viewing files and file information.
To delete a file in the current directory, you select the file with the highlight bar from the list provided by the FILER, and press the <Del> key (refer Figure). The file will be deleted. Multiple files can be deleted as well. To do so, you move the highlight bar through the list of files and select them with the F5 key. After all the files have been selected, they can be removed by pressing the <Del> key. FILER seeks confirmation from you before it does the delete operation.
FILER - Directory Contents
FILER offers you an option to either delete all the files in any of the subdirectories listed, or delete the entire subdirectory structure. You select the subdirectory in which you want to do the delete operation with the <Del> key. You can then select the Delete Subdirectory Files only option (refer Figure) to delete only the files contained within. The Delete Entire Subdirectory Structure option will remove the entire directory structure. In either case, FILER will seek confirmation from you.
FILER - Delete Subdirectory Options
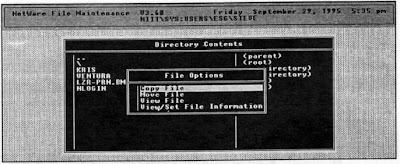
To copy files from the current directory, you select the file you wish to copy with the highlight bar. If multiple files are to be copied, you mark each one of them using function key F5. After selecting the Copy File option (refer Figure), you are prompted to enter the destination. The file(s) will then be copied.
FILER - File Options
To view the contents of a file, you select the file from the list provided, after which you will have to select the View File option to view the selected file's contents. If the View/Set File Information option is selected, you are provided information about the selected file.
The <Esc> key will take you out of any of the submenus to the next higher level.
The PURGE Command
To destroy confidential documents, we use a paper shredder so that even the torn pieces of paper cannot be put together. Similarly, if a confidential file is deleted and you do not want to risk someone salvaging the file and seeing its contents, you can use the PURGE command to remove it permanently. Files, once PURGED, cannot be recovered using the SALVAGE utility.
NetWare to the Rescue
Very often you delete files that are no longer of use to you by using the DEL command of DOS. It may happen that you inadvertently delete files that are needed. There is no need to panic. The NetWare SAL VAGE utility enables you to recover these files.
All you need to do is specify the directory from which the file was deleted, give the name of the file that was deleted, and the file will be recovered.
For instance, if you want to recover a deleted file FORMAT.COM from the directory UTILS, you invoke the SALVAGE utility from the NetWare prompt. The Main Menu as in Figure is displayed on your screen.
SALVAGE - Main Menu
You select the option Select Current Directory and you are prompted to enter the name of the directory, in this case VOL1:UTILS, from where you want to recover the deleted file (refer Figure down).
SALVAGE - Current Directory Path
SALVAGE will then take you back to the Main Menu, where you select the option View/Recover Deleted Files. You are then prompted to enter the filename, in this case FORMAT.COM (refer Figure down). The file will then be salvaged.
SALVAGE - File Recovery
A wildcard pattern match can also be specified instead of the filename. SALVAGE displays a list of files that match the wildcard pattern from which you can select the files that you want to recover. At any time during this operation, if you want to return to the NetWare prompt, you press the <Esc> key.
File Management in NetWare
Working on a node in Novell NetWare is as good as working on DOS, coupled with the advantage of having access to files on the server. NetWare allows you to use DOS commands to access files from the server. You are familiar with the tree-like directory structure of DOS and the fact that the NetWare structure is strikingly similar. Hence file management under NetWare will not pose much of a problem to you.
| Follow Up Next |
NetWare Commands
Any of the commonly used DOS commands, like DIR, DEL, REN, CD or MD give the same result in NetWare as they do in DOS. However, these commands may not work the way they are supposed to because of trustee rights and file attributes. For instance, you cannot see the contents of a file for which you do not have the Read right. A DIR command may tell you that a directory is empty, but the fact may be that you do not have the File Scan right in that directory.
Rights and attributes are not the only reasons for the failure of DOS commands to perform their desired tasks. For instance, if you specify the server and the volume name with the COPY command of DOS, it will not work.
Consider the directory structure given in Figure.
Directory Structure
If you want to copy a file SALEPKGE.BAT from the directory PROG of the volume VOL1 to the directory LIB of VOL2, then the command
C0PYV0Ll:PR0G\SALEPKGE.BATV0L2:LIB
will result in an error message being displayed.
You will encounter the same problem with all the other DOS commands because DOS does not support the concept of volumes. In such situations, where the use of the volume name is imperative, you have to use the equivalent commands provided by NetWare. These commands not only replace their DOS counterparts, but are more powerful and versatile. In case you do not know how to use a particular command, NetWare provides help for all commands through the HELP utility, which can be invoked by typing HELP at the NetWare prompt. Note that the NetWare commands possess a lot of options. Therefore, the slash (/) before an option and back slash (\) in path names can be used to avoid confusion although using the slash in path names is permitted.
| Follow Up Next |
Listing Directories
Assume you are working in the directory USER and want to see the contents of the directory LIB under the volume VOL2. You can use the NetWare command NDIR to list its contents, the syntax is:
NDIR [path] [/option..]
The output is very much the same as that of the DOS DIR command: the names of the files/directories contained therein, their size in bytes and the date and time they were last modified. In addition, NDIR displays the date and time the files/directories were last accessed, their owner's name and the attributes assigned to them
Just like the DIR command of DOS, the NDIR command can also be used with wildcards. The command given below restricts the display of information to that pertaining to files that have the extension TXT.
NDIR V0L2:LIB\*.TXT
Very often you find yourself wanting to display details of files whose names cannot be matched by a common wildcard pattern. For instance, if you want to get information on the files SALES.DBF and TWO. DAT, you are not able to do so with a wildcard match. NetWare allows you to specify more than one filename with the NDIR command as shown below.
NDIR ONE.DBF, TWO.DBF
To view subdirectory information only in the directory BIN, for example, you can use the /DO option along with the command as given below.
NDIR V0L2:BIN/D0
Similarly, to view file information only in the same directory, the command
NDIR V0L2:BIN/F0
can be issued.
You can get information on files created by a particular user through the /OWNER option with the command
NDIR /OWNER = USER2
In the above example, NDIR will give you information about all the files owned by USER2 in the current directory. You can also find out details of files that are not owned by a specific user. The command
NDIR V0L2:LIB /OWNER NOT = USER2
will give you information about files not owned by USER2.
The date of creation of files/directories can sometimes be of great help. For example, if you forget the name of a file in which you had stored an important letter, but remember the date, the twenty-third of November 1994, on which you had created the file, the command
NDIR/CREATE EQ 11-23-94
will list the files that were created on that day, from which you can find the name of your file. The command
NDIR/CREATE BEF 11-23-94
will give you the details of files/directories created before the twenty-third of November 1994, while
NDIR/CREATE NOT BEF 11-23-94
will give you the details of files/directories created on the twenty-third of November 1994 and after.
The command
NDIR /CREATE AFT 11-23-94
will give you the details of files/directories created after the twenty-third of November 1994.
| Follow Up Next |
Renaming Subdirectories
Just as you can rename files, NetWare allows you to rename directories as well. The command to do so is RENDIR. The syntax is:
RENDIR old-path-name new-name
When you rename a directory, you do not affect the attributes or drive mapping associated with that directory. You only change its name.
To change the name of the directory BIN in VOL2 to REPORT, you can give the command
RENDIR V0L2:\BIN REPORT
However, if you have mapped the directory to the G drive before giving the RENDIR command, you can use the drive name instead of the directory name as given below:
RENDIR G: REPORT
| Follow Up Next |
Copying Files
The command to copy files in NetWare is NCOPY. The usage of this command is similar to the COPY command of DOS. The advantage of using NCOPYis that you can copy files across volumes, which cannot be done through the COPVcommand as we have seen earlier. The syntax is:
NCOPY source-path destination-path
To copy all files from directory LIB to current directory, you can use the command
NCOPY V0L2:LIB\*.*
NCOPY can also be used to copy files from one directory in a particular volume to another directory in a different volume.
NCOPY VOL1:PROJ\*.* V0L2:LIB
will copy all the files from the directory PROJ in the volume VOL1 to the directory LIB in the volume VOL2.
Another Line of Defense
Passwords and rights are both excellent security features on NetWare. They are enough to ensure that all your files and directories are not tampered with. But NetWare provides another line of defense in the form of file and directory attributes.
Attributes are special properties assigned to files and directories. Attributes override rights and prevent tasks that rights would allow. For example, if USER8 has the Erase right in a directory PROGRAMS, he or she would normally be able to delete files in that directory. However, if the files have the Delete Inhibit attribute set, this would not be possible.
Lists some important attributes along with their description.
| Attribute | Code | Description |
| Delete Inhibit | DI | Prevents erasure of files and directories. Overrides Erase right |
| Hidden | H | Hides files and directories from the DIR command of DOS, but not from the NDIR command if you have File Scan right |
| Purge | P | Purges files as soon as they are deleted (The purge command is dealt with later) |
| Read Only | RO | Indicates whether a file can be modified. (The attribute automatically turns on Delete Inhibit and Rename Inhibit attributes) |
| Rename Inhibit | RI | Prevents renaming of files and directories |
| All Attributes | ALL | Provides all available attributes |
| Normal | N | Clears all attributes |
Selective List of File Attributes
To assign attributes to a file, the command to be used is FLAG. The syntax is:
FLAG [path] [flaglist]
You may issue the FLAG command without any parameters to view the attributes of all files in the current directory. To view the attributes of a specific file, you can provide the filename along with the command. The command given below will display the attributes of the file EMPDAT.DBF.
FLAG EMPDAT.DBF
Wildcard characters can also be used along with the FLAG command. For example,
FLAG*.TXT
would allow you to view the attributes of all files with the extension TXT.
The FLAG command, like all NetWare commands, allows you to specify a volume name along with the path. For example, to provide Read-only and Hidden attributes to all files in the PROJ directory on volume VOL1, you may issue the command
FLAG VOL1:PROJ\*.*RO H
To provide all available attributes to all files in the current directory, the command
FLAG *.* ALL
can be used.
All attributes from the files in PROJ directory on volume VOL1 can be cleared with the command
FLAG VOL1:PROJ\*.* N
While the FLAG command allows you to change the attributes of files, the attributes of directories can be changed using the FLAGDIR command.
The FLAGDIR command allows you to change only the following attributes:
- N - Normal
- H - Hidden
- P - Purge
- DI -Delete Inhibit
- RI - Rename Inhibit.
For a description of these flags refer to the table provided with the FLAG command.
Now that you know about rights and attributes, you should always ensure that you practice the following:
- Log out of LAN after every session
- Do not provide rights to users who you think may tamper with your files
- Protect all critical files using attributes
NetWare - Where Right is Might
In NetWare, working in a directory where you do not have permission should be avoided because you may be shocked when a simple command like COPY does not work. Consider the following situation. You have made the root directory your currently active directory, and have tried to copy a file CP.BAT from the directory USER1 to the root directory. An error message is flashed on your screen! You cannot conclude that the COPY command does not work on NetWare. The reason is simple. You do not have the right to create files in the root directory. What are these rights all about?
Trustee Rights
Each user on NetWare is given a set of rights and has to work under these restrictions. It is one way by which NetWare protects your directories and files. Any operation, like copying, creating or deleting files, is controlled by these rights. They are given to you when your login is created by the supervisor, and are referred to as trustee rights. By default, on creation, all user logins belong to the group EVERYONE. You may also be made part of other user groups and hence inherit all the rights assigned to these groups. Apart from this, like every other user, you are given a special directory where you are assigned very special rights. Ordinary users will not have any rights in this directory and the subdirectories created therein by you.
The Table lists some important trustee rights available on NetWare.
| Rights | Code | Description |
| Read | R | Allows the reading and execution of files |
| Create | C | Allows the creation of directories and files |
| Write | W | Allows the modification of the contents of files |
| Erase | E | Allows the deletion of files and the removal of directories |
| Modify | M | Allows the changing of attributes and the renaming of files and directories |
| File Scan | F | Allows the viewing of file names with the DIR command |
| Access Control | A | Allows the user to grant/revoke rights to/from other users |
Selective List of Trustee Rights available on NetWare.
How do you find out the rights you possess for a particular directory? The answer lies in the NetWare command RIGHTS, for which the syntax is:
RIGHTS [path]
If a path is not specified along with the RIGHTS command, NetWare assumes that you want to see your rights in the current directory. Your rights are displayed in the format shown in Figure.
You can specify a path as well as a volume name along with the RIGHTS command. For example, if you want to see your rights of the directory GAMES on the volume VOL2, you can give the command
RIGHTS V0L2:GAMES
If you map drive J: onto the GAMES directory of the volume VOL2, you can save yourself the trouble of typing the volume and directory names by replacing them with the drive name as given below.
RIGHTS J:
The RIGHTS command also lets you see the rights you possess for a specific file. To view your rights for the file WIN.EXE, you can give the command
RIGHTS WIN.EXE
A cumulative list of all your rights in all the directories and subdirectories can be seen using the WHOAMI command with the /R option. The output would be as in Figure.
NIIT\SYS:USERS\ESG\FFC |
Output of the RIGHTS Command
You are user USER1 attached to server NIIT, Connection 9 |
Output of WHOAMI /R Command
Granting and Revoking Rights
In the directory allocated to you, you are generally given all the rights that were listed earlier. Other users cannot access your directories, if you choose not to let them do so. However, there are certain situations under which you may want to share one of your files/directories with someone else on the LAN. You can permit this by granting rights to him or her for your files and directories by using the GRANT command. The syntax is:
GRANT rightlist [FOR filename/dirname] TO username/groupname
Rights that can be granted are:
- ALL
- Create
- Access Control
- No
- Read
- Erase
- Write
- Modify
- File Scan
The command
GRANT R W F TO USER2
will grant Read, Write and File Scan rights for the current directory to the user USER2.
There are times when you would like to allow all the users belonging to a particular group, access to your files and directories. Rather than granting rights to all the users individually, which could be extremely laborious, you can grant the same rights to the group as a whole. For example, to grant Modify and Access Control rights to the group STAFF for the directory PROGS, you can issue the command
GRANT M A FOR PROGS TO STAFF
If you would like to grant all rights to a user USER1 for the directory GAMES, the command
GRANT ALL FOR GAMES TO USER1
will ensure the same.
Apart from granting rights for a directory, the GRANT command can also be used to grant rights to a user for specific files. For example, Write and Erase rights can be given by you to USER8 for a file START.BAT, by issuing the command
GRANT W E FOR START.BAT TO USER8
Now that you know how to give other users access to your files and directories, the need may arise, in due course, to take away these privileges. This can be achieved through the REVOKE command, for which the syntax is:
REVOKE rightlist [FOR filename/dirname] FROM username/groupname
Rights that can be revoked are the same as those that can be given away, with the exception of the No rights option that is not available with the REVOKE command.
Consider a situation in which you no longer want a particular user, USER2, to view the contents of your files in the current directory.
The command
REVOKE R FROM USER2
will achieve this.
If you would like to take away the Access Control right from the group STAFF for the directory PROGS, you may use the command
REVOKE A FOR PROGS FROM STAFF
To remove all rights from user USER1 for the current directory, you could use either one of the following commands:
REVOKE ALL FROM USER1
or
GRANT N TO USER1
To revoke the Write right for the file START.BAT from USER8, you can use the command
REVOKE W FOR START.BAT FROM USER8
The granting and revoking of rights is subject to the possession of the Access Control right. If you do not possess this right, you will not be able to grant or revoke rights.
Drives
In NetWare, the user can assign each of the letters of the alphabet (from A to Z) to a drive. NetWare recognizes 26 drives. The NetWare drives are not physical drives, but logical drives. Each of the alphabets is a pointer that points to a particular directory in the file structure.
Local Drive
By default, NetWare assigns alphabets A to E to local workstation drives, i.e. floppy disk drives and hard disk drives. Thus, NetWare assumes that a workstation can have a total of 5 floppy disks drives and hard disk drives. These drives are called local drives since they are local to the workstation.
Network Drives
Drives F to J are assigned as the network drives. Drive F is the first network drive. That is why in NetWare installations, after you give the IPX and NETx commands, you change to the F drive.
In a typical NetWare setup, a file server may contain several volumes, and each volume may contain several directories and subdirectories. Each user may need to access directories and subdirectories in two or even three volumes. There would be three or four directories or subdirectories that a user would need to access frequently. For example, if you need to switch from
NUT\SYS:USERS\JOHN
to
NIIT\SYS:PUBLIC\FOXPRO
You can use a pointer that would point to a given directory in a given volume. Therefore, in the example given above, the user would need to use a pointer that points to the directory NIIT/SYS:PUBLIC/FOXPRO. This can be done with the help of MAP command. To point to the above directory, you need to give the command
MAP G: = SYS:PUBLIC\FOXPRO
Now, no matter which directory you are working in, you just need to give the command G: and you would be in the directory SYS:PUBLIC/FOXPRO. Note that you need not specify the server name. You have mapped the directory SYS:PUBLIC\FOXPRO onto drive G. You can similarly map other directories that you use frequently on drives H, I and J.
A drive here is a logical indicator that points to a particular directory.
Search Drives
A mapped search drive allows you to execute program files even if these files are in a directory other than the one in which the user is currently working. When a directory containing one or more executable program files is search-mapped on to a given drive, then these programs can be executed from any directory. If there is a program file called FOX.EXE that resides in the subdirectory FOXPRO in the directory PUBLIC in the volume SYS, you would need to search-map the directory SYS:PUBLIC\FOXPRO onto a search drive. NetWare looks for the program file FOX.EXE (which is in SYS:PUBLIC\FOXPRO) in the current directory and, in case it does not find it there, it would look for the file in all the search drives that have been mapped till the file FOX.EXE is found. In NetWare, the 16 alphabets from K to Z are designated as search drives. Thus, theoretically, you can assign search drives to search for program files in as many as 16 directories.
If you want to search map the file FOX.EXE in FOXPRO on to a search drive, you need to give the MAP command
MAP SEARCH1: = SYS:PUBLIC\FOXPRO
Now the command FOX can be given to execute the file from your current directory. NetWare assigns search drives, in reverse order of alphabets, i.e. drive Z is search mapped first, then drive Y, and so on.
Again, search drives are not drives in the DOS sense. They are pointers that help you point to a directory that contains program files so that you can access these files quickly.
It is not necessary that drives H to Z need to be used only for mapping search drives. They can be used for mapping network drives too, in case you run out of drives for mapping network directories. In case you have mapped all these drives, you can assign K, L, M and so on, to map directories.
Note: As soon as the user logs out, NetWare erases the mappings.
Displaying Mapped Drives
You may have mapped several network drives to directories, and may have search-mapped several search drives. To know how and where the drives have been mapped, the command MAP can be given at the command prompt. This will display the screen as follows:
Drive A: maps to a local disk
Drive B: maps to a local disk
Drive C: maps to a local disk
Drive D: maps to a local disk
Drive E: maps to a local disk
Drive F:= NIIT\SYS:\LOGIN
Drive G:= NIIT\SYS:\PUBLIC\WINDOWS
SEARCH1:=Z:.[NIIT\SYS:\PUBLIC\FOXPRO]
Drive G has been mapped on to PUBLICWVINDOWS in SYS volume. Only one search drive (Z) has been mapped.