DOS helps you organize files by creating directories. The directory structure in DOS is a multi-level tree structure where the directories and the subdirectories correspond to the branches and the files correspond to leaves. The directory structure of Novell NetWare is similar to that of DOS. When we talk about the directory structure in Novell NetWare, we are referring to the directory structure of the file server.
On the server, the top-most level in the directory structure is the volume. Each volume has a unique name. Each file server has at least one volume called SYS. NetWare creates it when the file server is installed. A file server can have other volumes besides SYS.
Why have volumes? Well, to answer this question, let us answer a related question about the DOS directory structure: why have directories and subdirectories? The primary reason is to have a logical storage of files so that a user can easily access them. The same reason applies for NetWare. The difference between DOS and NetWare is that NetWare adds another level on top of the existing directory structure in DOS. Thus you have:
Files, which are in subdirectories, which are in directories, which are in the volumes of a file.

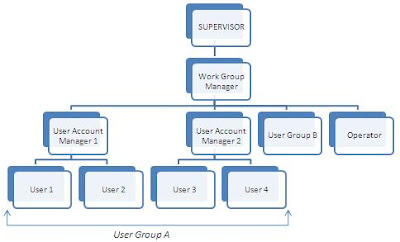
NetWare Directory Structure
Note: The number of subdirectories and files shown in Figure 1.4 is representative and does not indicate the exact situation in NetWare.
Dividing a hard disk into several volumes divides the disk into logical chunks.
Consider an office in which a NetWare LAN is being used by two departments, Marketing and Personnel. Apart from the SYS volume that would be created anyway, there are two other volumes; one for the Marketing department that would contain files related only to the Marketing department, and the other for the Personnel department containing files related only to the Personnel department. The employees in Marketing would have access only to SYS and VOL1 (containing marketing files), the Personnel employees would have access to files in SYS and VOL2 (containing personnel files).
A volume contains directories. In NetWare, the default volume, SYS, contains four directories: SYSTEM, PUBLIC, LOGIN, and MAIL. SYSTEM contains NetWare operating system files, NetWare utilities, and programs that are reserved for the Supervisor. PUBLIC contains program files that help to execute certain utility programs of NetWare. These can be used by regular users. The LOGIN directory contains files that help a user log in to NetWare. MAIL contains program files that help the user use NetWare's E-mail facility.
Apart from these four directories, additional directories can be created in the volume SYS. More volumes (in addition to SYS) can be created on the server hard disk. These volumes in turn, have their own directories. It depends on the supervisor to decide whether the organization needs more directories within SYS, or more volumes apart from SYS.
Each directory can be further divided into subdirectories and each of these subdirectories can contain files. A directory, instead of containing subdirectories, can also contain files.
In NetWare, the path for a Foxpro file can be given as:
NIIT\SYS:PUBLIC\SW\FOXPRO
which indicates that the file Foxpro is in the subdirectory SW, which is in the directory PUBLIC, which is on the volume SYS, which resides on the file server NUT. The server name and the volume name need not be included if you have a LAN with a single server and a single volume. In a situation where there are more than one server on the LAN, and each server contains several volumes, if the server and volume name is not specified while giving the file and directory name, NetWare assumes the current server and the current volume name.
If a LAN has more than one server, changing over from one server to another would require a fresh login from the user. If the user is currently working on the server NIIT1 and would like to work on the server NIIT2 as USER2, the command to be issued would be:
LOGIN NIIT2/USER2
Two additional points need to be noted here. While DOS recognizes only the backslash (\) for separating the levels of the directory structure, NetWare allows both the slash (/) and the backslash. Secondly, while DOS allows 127 characters in a directory path (including the drive letters and delimiters), NetWare allows 255 characters.